GPS spoofing, will we ever learn?
 Hat’s off to Professor Todd Humphreys and his grad students for not only demonstrating that GPS spoofing is possible but for doing so in such a dramatic fashion that they got the whole media world chattering about it. For instance, Fox News led their story with “The world’s GPS system is vulnerable to hackers or terrorists who could use it to hijack ships — even commercial airliners, according to a frightening new study that exposes a huge potential hole in national security.” While I think that’s an overheated conclusion, I suspect that we may need an even greater scare to finally build out a secondary form of civilian electronic position fixing…
Hat’s off to Professor Todd Humphreys and his grad students for not only demonstrating that GPS spoofing is possible but for doing so in such a dramatic fashion that they got the whole media world chattering about it. For instance, Fox News led their story with “The world’s GPS system is vulnerable to hackers or terrorists who could use it to hijack ships — even commercial airliners, according to a frightening new study that exposes a huge potential hole in national security.” While I think that’s an overheated conclusion, I suspect that we may need an even greater scare to finally build out a secondary form of civilian electronic position fixing…
What the University of Texas at Austin engineering team did is probably best described at their own site and in their YouTube video. In short, they were able to fool a serious GPS navigation system into thinking it was going some place it wasn’t, which is far more sinister than GPS jamming. No alarms sounded, and the autopilot started steering some place the crew didn’t realize their vessel was going. The fact that Humphreys managed to conduct this experiment on an 80 million dollar superyacht, with a proper captain and crew in whites, mainly served to make the story a lot more compelling.
 The fact is that GPS spoofing has been a worry for many years. One of my most memorable interviews took place in 2001 with a former administrator of the FAA named Langhorne Bond. We had a phone conversation that went on for hours and then he followed with a 116-page fax further detailing the dangers of over-dependence on GPS. The PMY article that followed — The Dark Side of GPS — quotes Bond thusly: “If we rely on GPS alone, there is the risk, indeed the likelihood, of multiple aviation and marine catastrophes.”
The fact is that GPS spoofing has been a worry for many years. One of my most memorable interviews took place in 2001 with a former administrator of the FAA named Langhorne Bond. We had a phone conversation that went on for hours and then he followed with a 116-page fax further detailing the dangers of over-dependence on GPS. The PMY article that followed — The Dark Side of GPS — quotes Bond thusly: “If we rely on GPS alone, there is the risk, indeed the likelihood, of multiple aviation and marine catastrophes.”
That was back when many experts like Bond were lobbying to convert the existing Loran system into a modern eLoran version that would nicely backup GPS using an entirely different technology that’s harder to jam or spoof. But the Obama administration killed the U.S. eLoran project in 2010 and at least some of the old towers were destroyed. Heck, the U.S. Congress just completely cut the FAA’s 20 million dollar budget for GPS modernization!
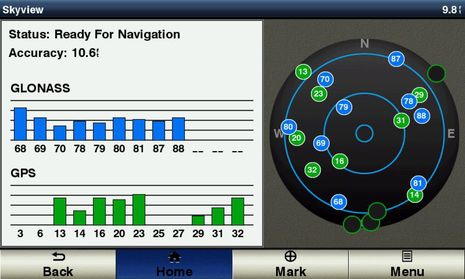 It’s great to see companies like Garmin incorporating the Russian GLONASS version of Global Navigation Satellite Systems — or GNSS, with “GPS” being the American version — into even the smallish GPSmap 741 seen above monitoring both systems from here in Camden, Maine. The more satellites the better for accuracy as well as reliability in difficult conditions. But I believe that GPS jamming is fairly easy to extend to GLONASS as well as Chinese and European GNSS in development, and it’s noteworthy that South Korea, which actually does get jammed by their northern neighbor, has decided to build an eLoran system.
It’s great to see companies like Garmin incorporating the Russian GLONASS version of Global Navigation Satellite Systems — or GNSS, with “GPS” being the American version — into even the smallish GPSmap 741 seen above monitoring both systems from here in Camden, Maine. The more satellites the better for accuracy as well as reliability in difficult conditions. But I believe that GPS jamming is fairly easy to extend to GLONASS as well as Chinese and European GNSS in development, and it’s noteworthy that South Korea, which actually does get jammed by their northern neighbor, has decided to build an eLoran system.
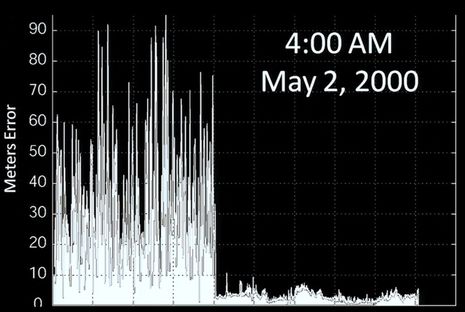
Then again, there’s never been a malevolent use of GPS spoofing that I know of, and I suspect that the spoofed White Rose of Drachs crew would have seen a problem before anything catastrophic happened, because they use other means of navigation like radar, depth sensing, and magnetic heading. Like we all do, right? I fear we’ll have to wait for a really good backup electronic positioning system, but in the meantime, I’m not sure there’s a better presentation on where “GPS” is heading, and the booby traps involved, than Todd Humrphey’s TED talk, which begins with the important slide below. The better it works, the worse it may hurt when it doesn’t.













There was a great interview about this which highlighted the less-talked-about threat from spoofing. A huge amount of our modern infrastructure, from the power grid to the telecom system, relies on GPS for highly accurate timing information. If you spoof the timing, all these systems which need to coordinate across long distances start loosing their ability to coordinate.
UK speeds ahead with rollout of eLoran stations to backup vulnerable GPS http://goo.gl/vmGXNL
The decision to de-activate Loran C was (of course), take your pick: dumb, short-sighted, malevolent, typical of a USCG that mostly comes from Kansas.
GPS has made cruising infinitely easier, but I have the Luddite credentials to say that anyone who depends on it is in danger of a very unpleasant surprise. Anyone going offshore from the US, even if only to Bermuda, without a plan for what to do if their electronic navigation fails, for whatever reason, deserves whatever happens.
Frankly, Michael, I think it’s pretty dumb to attack the U.S. Coast Guard. They are a small, relatively-underfunded government branch that’s being asked to do a LOT. The USCG attitude toward eLORAN was that other branches of government should help pay for it, which was completely reasonable.
Ben, I was not surprised when the e-LORAN system was killed here in the US. Typical political BS. I was one of the guys that had tried to pre-order the GPS/ e-LORAN units from a company you had posted about here on PANBO. Unfortunately DHS and our leadership are to blame for the destruction of e-LORAN not the USCG. Only in the US would we build a system, be prepared to turn it on then politicians decide to not move forward with it but to actually destroy some of the towers and make a news story out of it?
Bill
Actually, there is nothing new in this experiment.
GNSS (GPS, or GPS+Glonass) signal generators are commerically available for several years. For example, Spectracom offers their GSG-5 with many options like upgrade up to 16 channels (16 simulated satellites) or StudioView control software for simulation scenarios. GSG-6 could even simulate both L2, L2C and L5 frequencies. Then, you just have to add some low noise amplifier with good directional spiral antenna.
The only new aspect is that it was made by a couple of students with less expensive hardware. But if all that things are about hijacking the multi-million yacht or another vessel, nothing will stop some modern hijackers.
Ben, Great article on spoofing. The team at Digital Yacht have been working to create a more reliable positioning solution for a while and we’ve come up with our GPS150 DualNav solution. On a personal level, I think the introduction of GLONASS is a step change in navigation akin to GPS and AIS so we saw the opportunity to make a sensor that could integrate into legacy and current systems too – not everyone can afford to buy a new colour screen. We’ve set up a little microsite at http://www.dualnav.com to showcase the product and technology
Didn’t I read Dgps is spoofable with phoney beacons?
I have a Yeoman GPS map system that uses paper charts on a digitized table and a mouse/puck, when the electronics and the GPS fail you are left with a real chart, a great system.
Worth a Panbo review.
DGPS is also vulnerable to spoofing.
But, more independent channels of positioning giving more reliability in spoofing detection. For example, accelerometers and magnetic compass could give some velocity and direction readings to be compared with velocity and direction calculated from GNSS data. If there will be some significant specific error, GNSS navigation data should be treated like fake information. Then, of course, we should think about more traditional navigation aids and about contacting the authorities to let them know about possible attempt of hijacking.
I’ve used to learn electronic warfare technologies in university and now I feel, that these methods could gradually come into our regular life. In my student times, simple jamming noise generator was huge like a car and intended for military use only. Now you could get it for fifty bucks from China, fit it into your pocket and put down cellphones, GNSS and wireless networks in sixty feet around you.
Similar article with a few other details:
http://arstechnica.com/security/2013/07/professor-spoofs-80m-superyachts-gps-receiver-on-the-high-seas/
Ben-
Virtually any broadcast electronic positioning system is vulnerable to spoofing or jamming. Extra effort has been made on Aviation GPS receivers to detect spoofing for this reason.
Spoofing will shortly become more difficult when the second “GPS” system from the EU (Galileo) is built and made operational in a few years. With a duplicate satellite navigation system working on spectrum adjacent to GPS (New receivers will be needed) with a different modulation scheme. It will then be possible to constantly compare the two GNSS positions to detect and defeat spoofing.
GPS will also soon be augmented with a second broadcast frequency referred to as L5 (L1 is currently used for Civil Navigation and L2 used with L1 for precision ground based positioning to within 1 cm). When receivers with both L1 and L5 are available then we will see significant enhancements to protection from spoofing, particularly when combined with Galileo (which also has E1 and E5 frequencies).
So a new generation of GNSS (Global Navigation Satellite Systems) will evolve over the next decade to advance what can be done for protecting a broadcast navigation scheme.
I highly doubt there will be any secondary broadcast system developed. Instead the MIL is working on “personal navigation” or independent navigation that does not rely on any broadcast system for navigation. There will be a rekindling of older technologies used to implement self navigation capabilities. Doppler navigators at new exceptionally high RF frequencies and very low cost inertial sensors among other ideas (Cell tower angle of arrival etc) may be coupled together to create such self reliant navigation systems.
Currently the first generation of personal navigation with high accuracy is being developed for “first responders” such as fire fighters who can get lost inside large buildings and require room by room location capability with no GPS or other broadcast signals. Honeywell currently makes such a system.
More compact and reliable systems will be added.
Finally, commercial ships are required to carry inertial navigation systems in addition to GPS. These systems are designed to provide independent navigation in lieu of or in addition to GPS to prevent theft and accidents.
Thanks, DaveV, but isn’t GLONASS already the second GNSS and the EU’s Galileo will be the third?
Also, did you see the link to funding problems with GPS modernization?
http://www.insidegnss.com/node/3615
Ben-
Yes technically GLONASS is the second and Galileo the 3rd. However, the Galileo system has an army of companies developing dual GPS / Galileo receiver chip sets. As indicated on the Digital Yacht GPS150 website GLONASS has only recently become a dependable GNSS. Chip sets for GLONASS receivers are therefore only now becoming useful.
Yes funding for GPS III to get the L5 frequency rolling is now delayed due to funding issues but it will eventually become real – perhaps ushered in when aviation safety issues cause some near miss or some significant economic impact. Perhaps Mr Obama should be stumping for GPS improvements for safety, economics and jobs instead of more asphalt.
The solution to Spoofing is advanced receiver development. Google search “GPS spoofing detection” and under Scholarly Articles you will find several very good examples of means to improve GPS receivers to automatically detect and reject spoofing.
Where is the outrage that receiver manufacturers are not doing more to ensure safety? What would have happened if critical PLB / EPIRB position data had been spoofed during the University of Texas GPS spoofing publicity stunt?
I am intrigued by the Digital Yacht GPS150 that claims to not only use GPS and GLONASS but is ready for the Galileo system when it become operational in 2018. I’d like to know if they have specifically added features to detect and reject spoofing with the availability of multiple GNSS systems in their receiver system.
It would be interesting to see if other Marine GPS manufacturers are willing to indicate if they have done anything to significantly reduce GPS receiver vulnerabilities with advanced algorithms / dual / triple GNSS tracking or other methods as part of product development and not just touch screens with uber-fast redraw times.
Spoofing is detectable and therefore preventable – it takes investment and consumer demand to make it real in products. It is far too easy to blame the GPS system itself as being some how at fault.
Perhaps a special report on receivers like the GPS150 DualNav could focus on their ability to specifically provide additional reliability and prevention of navigation errors due to spoofing or jamming would be a great public service.
Glonass is the second GNSS, but, as I’ve already mentioned above, all these civil systems are affected by commercially available test signal generators.
But military GPS receivers could easily detect spoofing by decrypting code sequences transmitted by each GPS satellite. Civil receivers just comparing the delays when getting these sequences, while military ones could really understand the encrypted information.
If such a method of coding will be available for civil receivers (in future versions of GPS satellites), spoofing problem will be almost solved, because testing generators could transmit just their own fake codes instead of actual ones.
Man intending to jam a gps tracker installed by his employer, is noticed by local Airport. FCC fined man $ 31,875, Employer fires man.
http://autos.aol.com/article/new-jersey-gps-airport-newark-gary-bojczak/
What was he using, a left over lightsquared transmitter ?? You would think a little automobile based jammer would go unnoticed.
Dan that’s hysterical but it could have been true. What a mess that would have been.
My head hurts thinking about it!
Bill Lentz
Wireless One
Dan and Bill, the tiny jammer this fellow was using was causing a problem because he was fairly close to a receiving site that was providing GPS correction data to aircraft in conjunction with a precision landing system. The device he used is low power, but it was sufficient because it was on the exact frequency band of GPS, not nearby like Lightsquared intended to be. GPS satellites are very low-powered transmitters themselves, hence the problem.
Hartly I fully understand the mechanism, engineering and what the guy was using including the full ramifications of the use of a GPS jamming device. One could simply use a noise figure meters (head) and amplify it’s broadband noise with a class A amplifier if they wanted to do harm.
However I’m not sure if you are defending L2’s band plan?
If L2 was allowed to continue the end result would have been a disaster for those using devices that depend on GPS when they got close to any L2 transmitter. In the cellular industry it’s known as the near/ far problem.
Filters placed after the noise source do little if anything when the mode of interference is simple RF overload and the lack of dynamic range in a receiver trying to capture signals +50dbm
Bill Lentz
MV; WIRELESS ONE
Little Egg, NJ
Hi Bill,
Not a chance! Lightsquared was way out in the weeds, IMHO, and was rightly slapped down, in spite of (or more correctly, especially because of) the amount of political “lubrication” they tried to apply. What I was trying to convey was that Lightsquared was a potential problem because of the high level of power they wanted to use on adjacent spectrum, while the jammer in question was effective at much lower power because it was right “on channel” with GPS.
As you clearly realize, on-channel noise jamming is VERY difficult to overcome, while on-channel “spoofing” is another kettle of fish entirely. There are some VERY clever cellular jammers out there, btw – not just noise sources.
I regard this as a publicity stunt, not something that is likely to ever happen. It does raise awareness of the limitations of GPS.
This kind of spoofing is just a bizarre case multipath, which is a well known problem. Although a reflected signal doesn’t usually arrive before the line of sight one, which could be the case here.
This attack is targeted at one GPS antenna position. Any other GPS antennas on the ship would also be affected but not necessarily in the “correct” manner for their relative positions.
In the same way, a GPS compass would find the phase difference relationships confusing since the signals come from the wrong directions.
This is an interesting article. GPS spoofing has been a problem for awhile now. One area that is being affected by this is the military. Over the past few year, the military has increased their use of GPS systems. It is amazing how technological advanced they became. Fortunately, the accomplishments of SAASM has helped with these sorts of situations.
Or how about pirates spoofing AIS man overboard devices to lure in good Samaritans?
http://arstechnica.com/information-technology/2013/10/avast-new-hacks-could-steer-ships-into-pirates-grasp/
(Thanks to Nik for the link)
More AIS hacking! Looks humorous and superficial at first but some of the exiperiments actually get deep into the anti-collision system:
http://www.technologyreview.com/news/520421/ship-tracking-hack-makes-tankers-vanish-from-view/?utm_campaign=socialsync&utm_medium=social-post&utm_source=twitter
The writer of the article doesn’t understand.
1) IMHO it is pointless to encrypt a many to many conversation, that everyone would have the decryption key for. Incorporate the most comprehensive encryption, and someone can still buy or steal an AIS transmitter from a ship and feed in fake GPS location data. Someone can still selectively make one or many vessels disappear (jam the specific time slot) by combining the decrypt output of an AIS receiver with a custom made transmitter.
2) Had such a useless capability been included originally that would have vastly reduce the number of time slots / reduce the number of ships that could report their position in the same geography.
AIS is now headline news in the BBC smartphone application, or find it here
http://www.bbc.co.uk/news/technology-24586394
The article is very far off base. The technology is being called “legacy” and “outdated”, principally because it is lacking encryption / protection from being hacked. (like GPS)
Funny, just last year AIS owners were considered early adopters.
So how exactly do you have an AIS system that is un-hackable? I still believe it’s pointless to encrypt data you want EVERYBODY to be able to read.
Dan, check out http://en.wikipedia.org/wiki/Public-key_cryptography – it is indeed possible to have an encrypted message that all can decrypt, but no one else can encrypt. It’s a form of transmission authentication in this case.
It is interesting to find this popping up everywhere now ( http://www.heise.de/security/meldung/Manipulation-von-Funkdaten-Schiffe-versenken-mit-AIS-Hacks-1980065.html if your German is good enough). Even most of the people who visit the Heise-website (highly technical computer site) don’t fully understand the system.
TrendMicro, where the original report comes from, seems to have a good PR department but lacking on the technical knowledge.
I am just shaking my head, while reading though the articles linked to in this forum.
BBC: “The AIS system is used to track the whereabouts of ships travelling across the world’s oceans”
I don’t think so. Not by using an VHF radio with a very limited range. If the guys would have looked at the marinetraffic website, then they might have seen, that there are no ships more then 40 to 60 miles of the coasts. Hmmm…
And here is Technologyreview: “The researchers showed that their spoof signals were faithfully reproduced on the maps provided by online services that monitor AIS data, such as this one. ”
When I am out sailing, I don’t worry about what is going on the marinetraffic website. I prefer to look at my chartplotter, which gives me the AIS positions of whatever my receiver can receive.
I think the main problem is, that these reports come from an internet company, which doesn’t understand that AIS happens on the water and that is where it matters and the internet is an imperfect virtual copy of what people manage to read through their AIS receivers. One of the reasons, I would never use AIS apps via the internet on the boat.
Well, satellite reception of AIS signals is getting more widespread. There is an industry, still pretty infant, but growing, that seeks to capitalize on AIS signals by selling cargo-movement data to interested parties.
I don’t really think anyone uses the AIS traffic sites for navigation — it would be most unwise.
Carsten, I fully agree that it’s disturbing how many tech writers misunderstand the AIS system. In fact, I wrote a comment to that effect on the Ars Technica pirate story ( http://goo.gl/7ZgxCW ).
Unfortunately a lot of boaters are confused about this too, jumping to the conclusion that sites like Marine Traffic represent complete and official data. I love MT, and encourage people to set up shore receivers to make it better, but it surely does not offer complete coverage and probably never will.
So, please everyone, when you see AIS misinformation out there, step in and try to straighten readers (and writers) out. Thanks!
Informed commentary on AIS spoofing from Jeff Robbins of Vesper Marine:
http://blog.vespermarine.com/2013/10/ais-spoofing-should-we-be-concerned.html
Radar can be jammed did that stop the US military or ships from using it? Heck no in fact during the Vietnam War the US used TRAC29 high power cavity 7289 the Ceramic version of the 2C39 triode tube transmitters to jam enemy radar. Many US hams converted these units to water cooled high power 100 watt linear (class AB1) operation on the 2304MHz band.
Bill Lentz
Wireless One
Little Egg, NJ
I came across another version of the piece today that said with a 700 EUR AIS transponder remote control commands could be sent to prevent other vessels from transmitting. I’m not sure what equipment is being used.
But indeed, all AIS transponders are required to respond to channel management messages. However, there are some safe guards in place. For example, current Class B compliance requires that the channel management messages must come from a verified base station. This is done by looking at other messages sent by that station and its MMSI. To help prevent impersonating basestations, under the standard a Class B can’t be configured to use a basestation MMSI.
Channel management messages can also be sent via DSC to an AIS transponder. And DSC is of course also used for all sorts of things including search and rescue. Same story….